By Stefano Bellasio
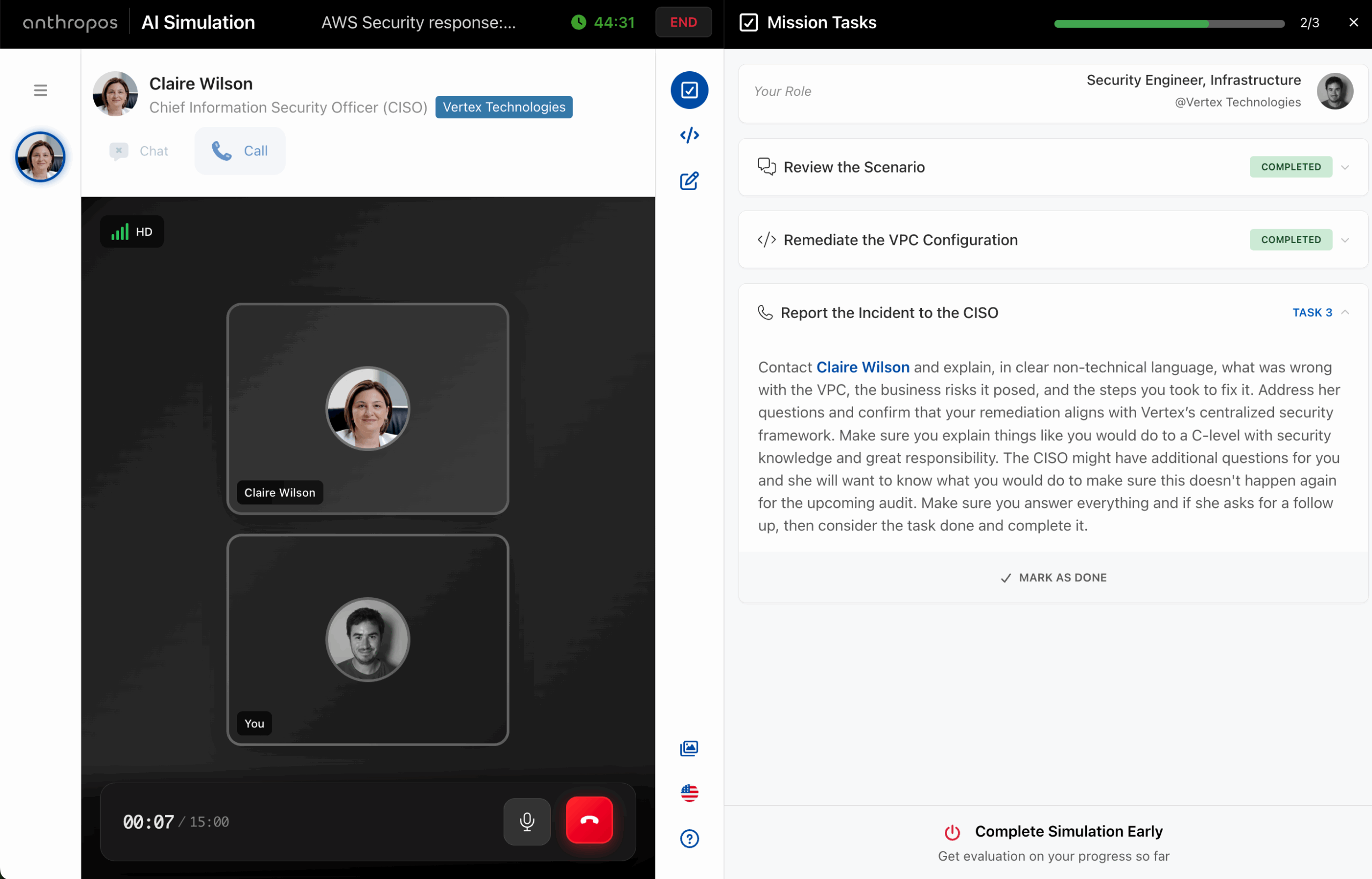
At Anthropos, AI Simulations are how companies verify and develop skills. They're immersive, real-life workplace scenarios where employees and candidates interact with AI-powered actors — through voice calls, chat, code editors, and documents — to demonstrate what they can actually do on the job. This month, we've made major improvements to how simulations feel and ...

For a long time, workforce decisions were made based on manager input, tenure, or simple performance reviews. Who’s ready for promotion? Who needs support? Who’s at risk of burnout or churn? These questions were often answered by what someone “felt,” not what the data showed. But as companies grow, reorganize, and integrate AI into more ...

For decades, companies have made talent decisions based on static snapshots: job titles, performance reviews, self-assessments. But in today’s environment—where roles evolve rapidly, AI is reshaping workflows, and skills become outdated in months—those snapshots are no longer enough. The real competitive advantage lies in understanding what your people can actually do right now, and how ...

Hiring the right software engineer is just the beginning. Today that means finding someone that has great coding skills but also the ability to pick up Cursor, Claude Code or other AI-based solutions to make their productivity 2x/3x the one of a normal engineer. Still, it doesn't change the fact that once they’re in, the ...
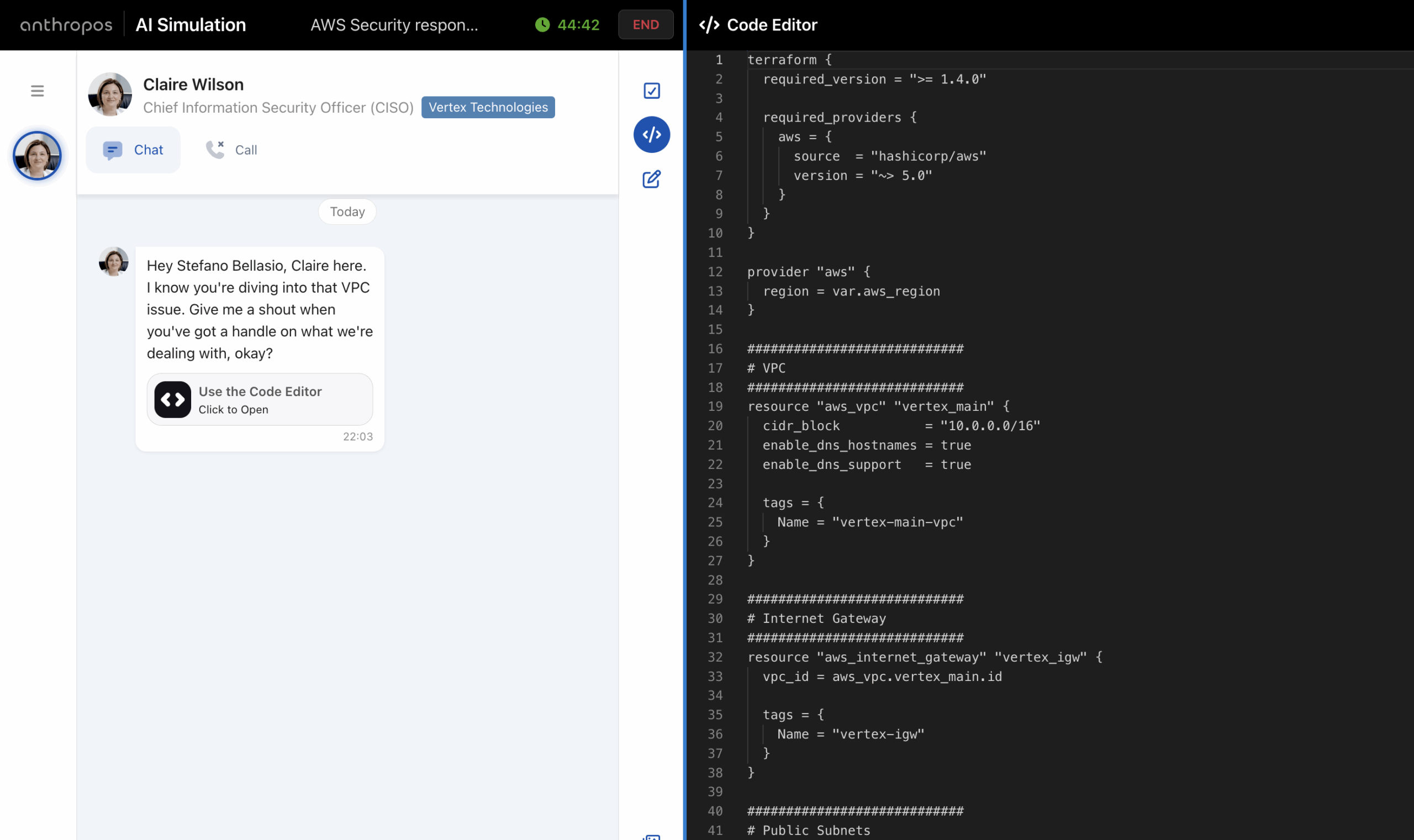
Hiring engineers has never been easy, but in 2025 it’s becoming one of the most complex challenges for companies across industries. The rapid evolution of technology, coupled with the widespread use of AI-assisted tools, has fundamentally changed how software is built—and how developers should be evaluated. In a world where AI is helping developers being ...
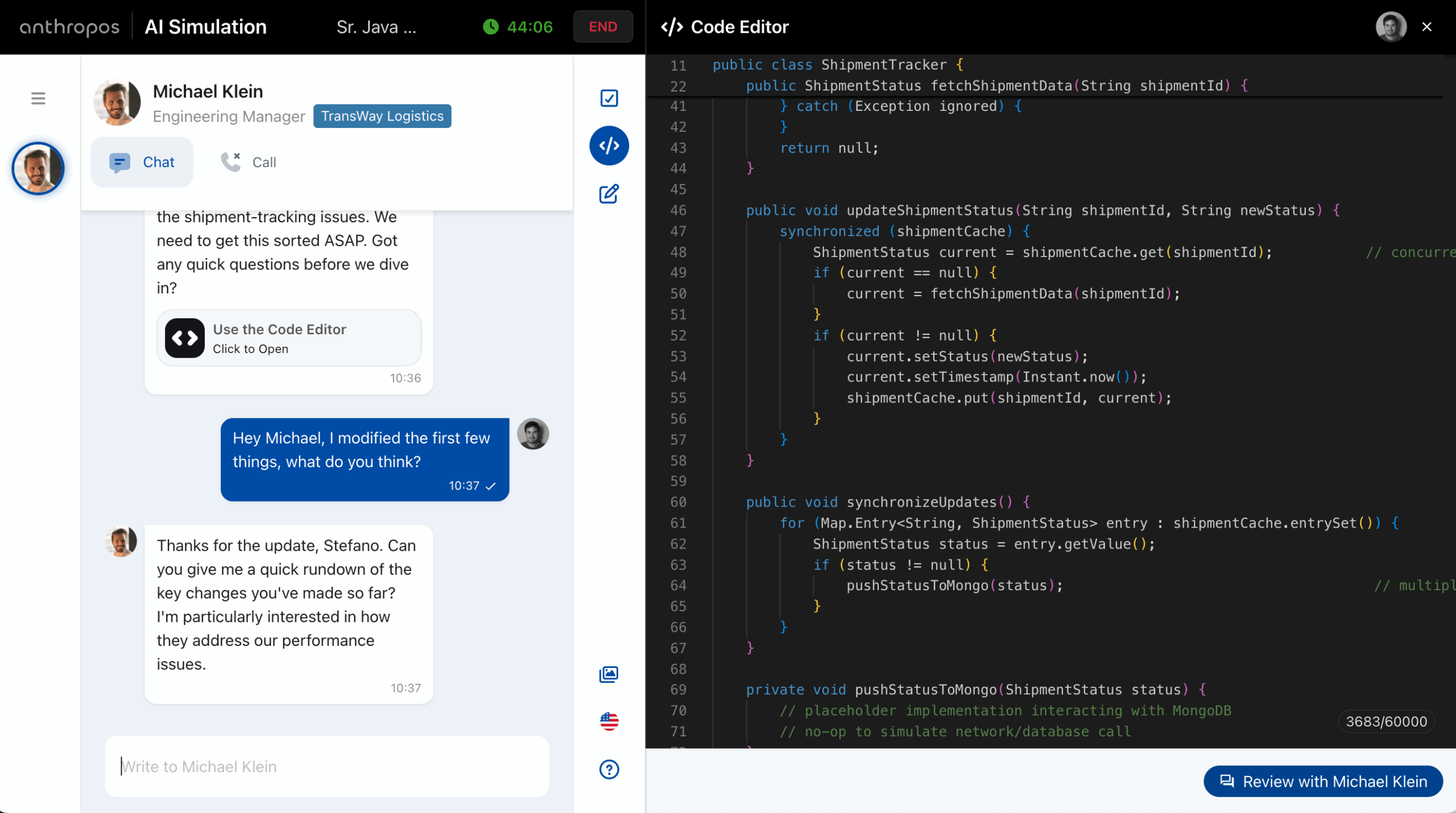
In today’s AI-augmented development landscape, hiring a talented developer is only step one. The harder and more crucial challenge is making sure they stay sharp—ready to adapt to shifting technologies, changing architecture choices, and increasingly cross-functional expectations. The future of software development isn’t just about coding anymore. It’s about learning quickly, collaborating well, navigating ambiguity, ...
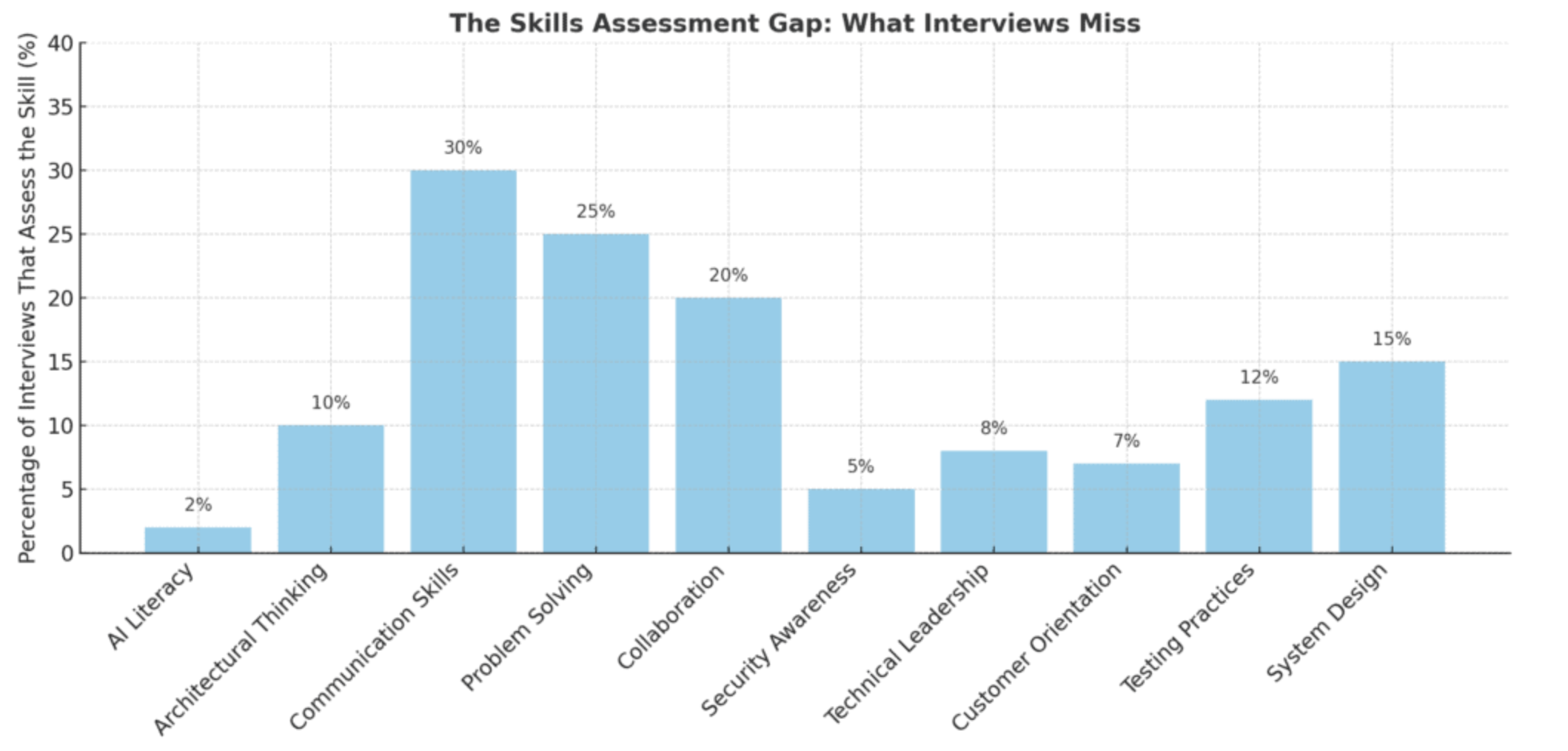
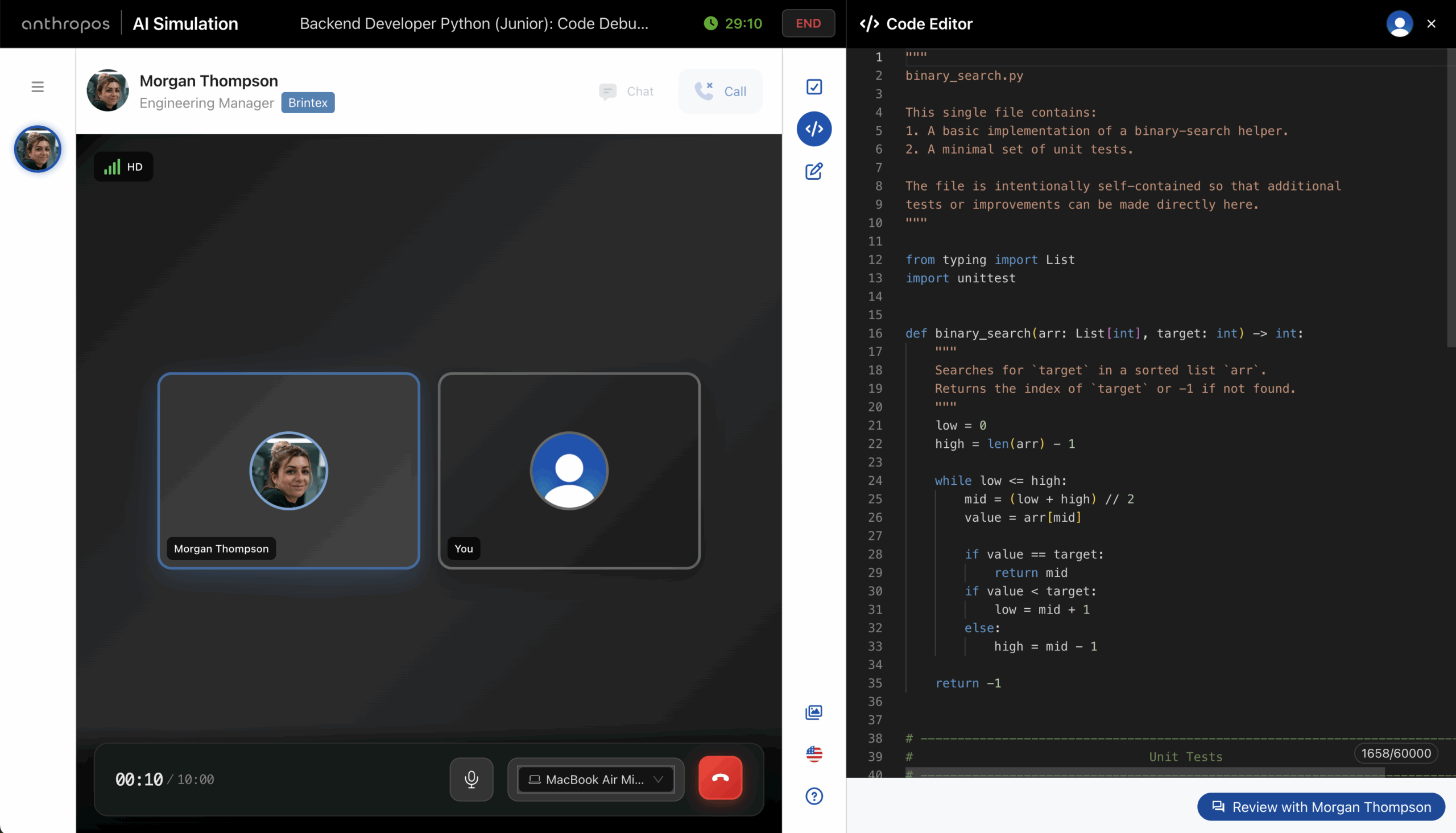
For years, the live coding session has been the gold standard for hiring software engineers, front-end developers, and other technical roles. A candidate joins a Google Meet or Teams call, a couple of senior engineers log in, and for the next hour the candidate is expected to solve coding challenges live, while explaining their thought ...
By Stefano Bellasio
The way companies evaluate and hire software developers is changing faster than ever before. For years, technical hiring relied heavily on coding tests and algorithm challenges—often delivered through platforms like HackerRank or similar tools. These assessments asked candidates to solve abstract problems under time pressure, with the goal of proving raw coding ability. While they ...